Confidential Data Pools with Enclave
CDPs let multiple agents and entities compute together — privately, verifiably, and without intermediaries. This post explores how Enclave makes them possible, and what they unlock for collaborative AI, finance, and research.

Computation is not simply data processing. In an increasingly interconnected planet, we’re discovering how deeply it shapes collaboration, interaction, and how we make sense of our worlds. Yet, current computational frameworks often isolate data in solos, not only out of fear of exposure or regulatory risk, but because access is rarely reciprocal, exposing imbalances in who benefits from shared information.
Confidential Data Pools offer a way forward: multiple parties can compute over encrypted inputs without relying on trusted intermediaries or exposing data to anyone, even each other. Enclave’s Encrypted Execution Environments (E3s) make this possible through a decentralized network of ephemeral keys and cryptographic verification, with no exposure at any stage. Only verified outputs are ever decrypted and shared.
This article explores how E3s enable Confidential Data Pools in practice, and what that unlocks for sectors like healthcare, finance, and AI.
Limitations of Existing Approaches
Current approaches to privacy-preserving data collaboration typically fall into three categories:
- Multi-Party Computation (MPC) Frameworks: These systems use secret sharing and collaborative protocols to compute across private inputs. However, they usually require tightly coordinated parties and highly customized computations, limiting scalability, flexibility, and general use.
- Trusted Execution Environments (TEEs): TEEs offer hardware-based security but rely on centralized vendor trust and have well-documented vulnerabilities to side-channel and supply-chain attacks. (For a deep dive into TEEs vs E3s, read our blog post.)
- Federated Learning: FL keeps data local while aggregating insights globally. While useful for many statistical applications, it’s tightly coupled to specific workflow types and doesn’t generalize to arbitrary computation or multiparty coordination.
The limitations of today’s privacy-preserving systems aren’t just technical; they’re architectural. Each approach offers partial solutions, but none fully address the core problem: How can independent entities compute together over encrypted data without exposure, centralized custody, or trusted operators?
Confidential Data Pools as Design Pattern
Enclave’s Confidential Data Pools (CDPs) make it possible to compute with others, not just protect against them. They’re not a product, but a pattern: a reusable structure for collaborative computation across private inputs. Unlike privacy pools, which focus on transactional anonymity, CDPs enable shared, verifiable computation, without delegating trust or exposing data.
Enclave enables this pattern through Encrypted Execution Environments (E3s), a modular system for multi-agent coordination across encrypted inputs. Each party retains control, and computation is performed without shared custody, central operators, or trust assumptions.
🧑🤝🧑 Supports Multi-Source Inputs: E3s facilitate computations across data from separate and potentially distrustful providers.
🔐 Maintains Continuous Encryption: Data remains fully encrypted during submission, computation, and output generation.
🛡️ Preserves Data Custody: Data providers retain full control over their inputs. No need to hand off raw data or delegate access to third parties.
🔍 Verifiable at Every Step: Each phase (input integrity, key generation, computation, and decryption) is validated and provable, without relying on hardware-based trust.
🔑 Distributes Trust: Key generation and decryption are handled across decentralized Ciphernodes, ensuring no single party ever holds full access.
💨 Executes Ephemerally: Each E3 instantiates with single-use keys that are discarded after execution, minimizing long-term risk and attack surface.
How E3s Make Confidential Data Pools Work
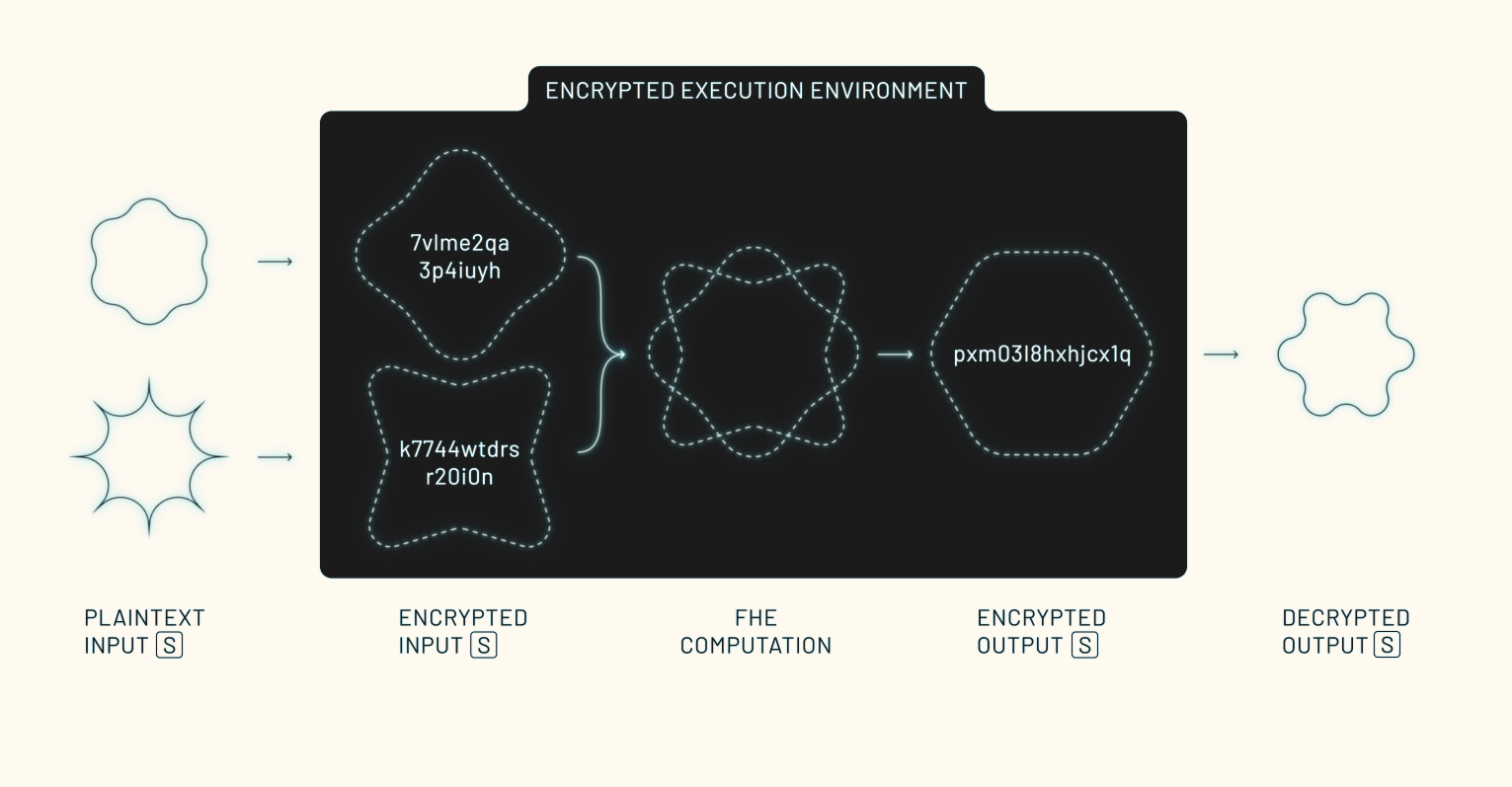
CDPs depend on three core guarantees:
- Private inputs: Data stays encrypted at every stage (submission, execution, and output generation).
- Verifiable outputs: Every step of the process is proven correct using zero-knowledge proofs (ZKPs).
- No third-party custody: No third party, including the network running the computation, ever gains access to raw inputs.
These guarantees are enforced by E3s, which act as ephemeral, verifiable runtimes for encrypted collaboration. Each E3 facilitates confidential computation across multiple parties in a multi-agent system, with no shared custody or trust assumptions.
The architecture relies on a novel combination of the following:
- Fully Homomorphic Encryption (FHE) allows arbitrary computation on encrypted inputs.
- Zero-Knowledge Proofs (ZKPs) verify each phase of execution, including input integrity and decryption.
- Distributed Threshold Cryptography (DTC) manages ephemeral keys across Ciphernodes — no single point of failure or full access.
- Decentralized coordination ensures that execution is permissionless and reproducible, without centralized control.
What Confidential Data Pools Make Possible
With this infrastructure in place, CDPs create a more equitable foundation for shared analysis and decision-making, enabling collaboration without reinforcing the asymmetries that often arise from imbalanced data access. By keeping inputs encrypted and sharing only verified outputs, Enclave reduces the possibility that one party extracts disproportionate value or arbitrages the difference.
This makes new forms of collaboration viable in contexts previously constrained or impossible due to privacy risks, regulatory complexity, or institutional silos.
Real-world applications include:
- 🏥 Collaborative research across hospitals or labs without sharing patient data.
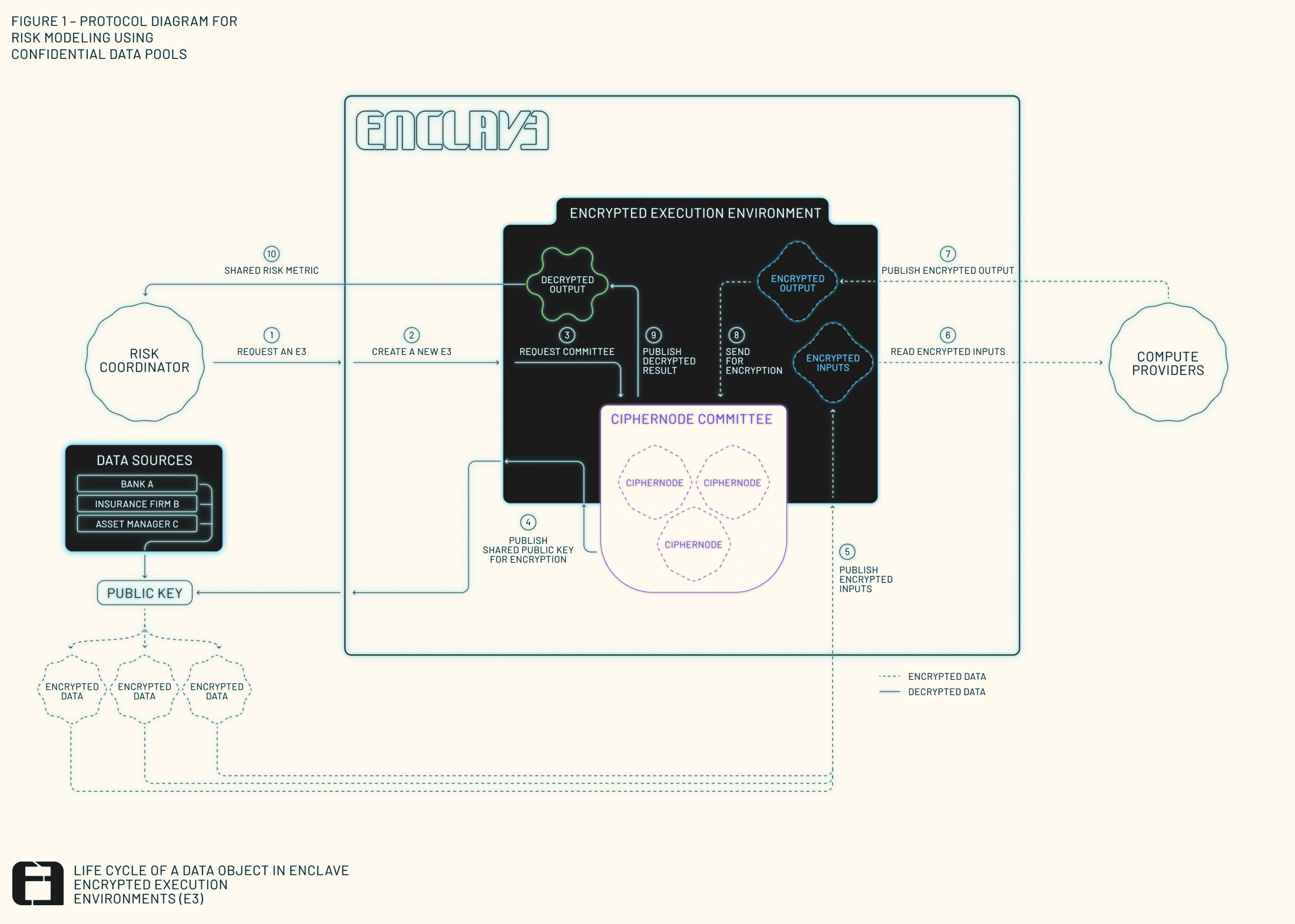
- 💸 Risk modeling between financial institutions without exposing proprietary portfolios (see Fig. 1)
- 🧠 Shared AI infrastructure that draws on encrypted datasets without breaching confidentiality.
- 🌎 Climate modeling that integrates sensitive data while preserving competitive boundaries.
Deploying Confidential Data Pools in Practice
Enclave provides the modular infrastructure that makes Confidential Data Pools a practical tool for secure collaboration. By keeping inputs encrypted, discarding keys, and validating computation through cryptographic proofs, it reduces liability and attack surface without compromising usability.
For developers, this means composable patterns for secure multi-party workflows, without building from scratch or navigating complex custody models.
For organizations, it means the ability to collaborate across sensitive datasets with regulatory confidence and verifiable integrity, without reinforcing the information asymmetries that typically come with data aggregation.
Confidential Data Pools put Enclave’s broader philosophy into practice: enabling computation as collective coordination, embedding trust into execution, and fostering privacy in relation, not isolation.
Get Started With Enclave
- Read the whitepaper for protocol details.
- Follow the Quick-Start Guide to launch your first E3 program.
- Join the Community Telegram for support and collaboration.
Enclave is an open-source protocol for Encrypted Execution Environments, with Gnosis Guild as its initial development team. Follow us on X, Farcaster, or subscribe to the blog for updates.
