Enclave Community Update no°1
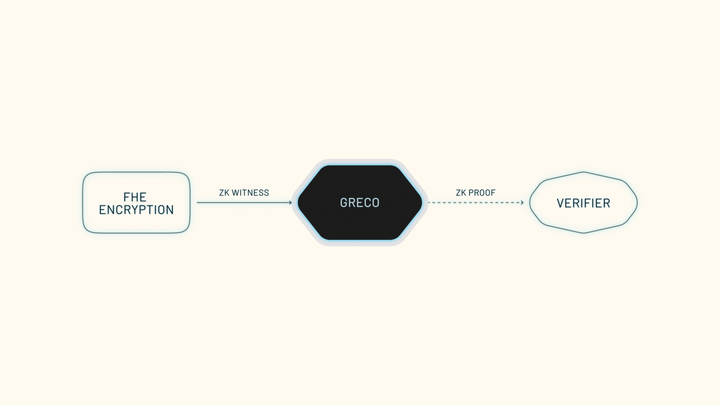
Happy New Year, privacy builders & systems alchemists! For those new here: Enclave is an open-source protocol for collaborative confidential compute, enabling shared computation with verifiable outcomes, without exposing underlying data. We’re kicking off the year by preparing for a public testnet, pushing forward our secret ballot protocol and