An Introduction to Encrypted Execution Environments
E3s enable secure, privacy-preserving computations over multiple inputs of encrypted data, enabling a new class of applications—from secret ballots to confidential data pools.

Computation is the medium of the 21st century. It's not merely a technical utility to facilitate socializing and consuming content through rectangular screens, but a means to orient ourselves within our broader social, economic, and technical systems. Computation can be at once personal and political, local and planetary, a site for artistic meaning and an actual property of physical materials, woven into our external environments. It's even quite magical:
computers think using etchings in poisoned sand and measure time using vibrating crystals so if you were looking for magic you found it
— Computer Facts (@computerfact) April 20, 2016
As our worlds become further saturated in data, computation increasingly shapes how we relate to and interpret our realities. Not just a tool for data processing, computation has become a mediator of power, knowledge, and agency — structuring the ways in which we interact with the world and enhancing our perception of broader systems. Take climate change, for example. Without computing on climate-related data such as CO₂ emissions, deforestation rates, and sea temperatures, our awareness, understanding, and ability to respond to climate change would be limited at best.
Computation breathes life into data, helping us foster new relational forms and sense-making modes — a dynamic facilitator for comprehension and context building that allows us to better understand our function, position, and agency within complex systems.
But as our reliance on computation grows, so do our concerns surrounding data security, privacy, and trust.
Challenges in Today’s Computational Landscape
Our current computational ecology struggles to meet the demands of our increasingly data-driven worlds. While issues like mass surveillance persist, data breaches, attacks, and privacy violations are also becoming more pervasive, exposing the risks in how we manage and compute over sensitive data. These vulnerabilities seed mistrust in our systems, leading to prohibitive regulations and reluctance to share or collaborate on data, which stifles innovation in our technical infrastructures.
Here are three issues preventing us from fully realizing the potential of our data-rich worlds:
- Data is traditionally vulnerable by default: Sensitive data is often exposed at some point in traditional frameworks, especially when organizations seek to share or compute over it. Without safeguards, the risk of breaches or ethical misuse grows, making privacy and security existential concerns.
- Trusted solutions can’t be fully trusted: Systems that rely on trusted intermediaries — such as cloud providers or trusted hardware — are prone to inefficiencies, vulnerabilities, and single points of failure, which can compromise the correct execution of computations and the privacy of data.
- Data regulations are complex and introduce risks: As the complexity and number of data privacy regulations like GDPR increase, organizations face growing complexity and liability, especially when lacking tools to process data securely and meet compliance standards.
These challenges have led to the exciting development of new computational frameworks, such as fully homomorphic encryption (FHE), zero-knowledge proofs (ZKPs) and multi-party computation (MPC), which address contemporary privacy and trust needs in unique, forward-thinking ways. But to date, no solution in isolation has been able to perform computations over encrypted data from multiple sources without exposing data to an operator or trusted hardware at some point in its lifecycle.
It is within this context that we introduce Encrypted Execution Environments.
Encrypted Execution Environments: A New Class of Secure Computation
Encrypted Execution Environments (E3) takes a multiplayer approach to data processing, enabling secure, privacy-preserving computations over multiple inputs of encrypted data. For instance, imagine an organization holding a secret ballot election, where the votes are counted and outcome revealed without ever exposing individual votes to anyone at any time. Or consider a healthcare researcher analyzing encrypted patient data to study treatment options, with multiple hospitals offering data without violating anyone’s privacy.
By integrating fully homomorphic encryption (FHE) with a novel combination of zero-knowledge proofs (ZKPs) and distributed threshold cryptography (DTC), E3 guarantees not only the correct execution of arbitrary computations over encrypted inputs, but also that the data remains encrypted throughout the entire computational process — whether it’s counting secret votes or analyzing private patient data (see Figure 1).
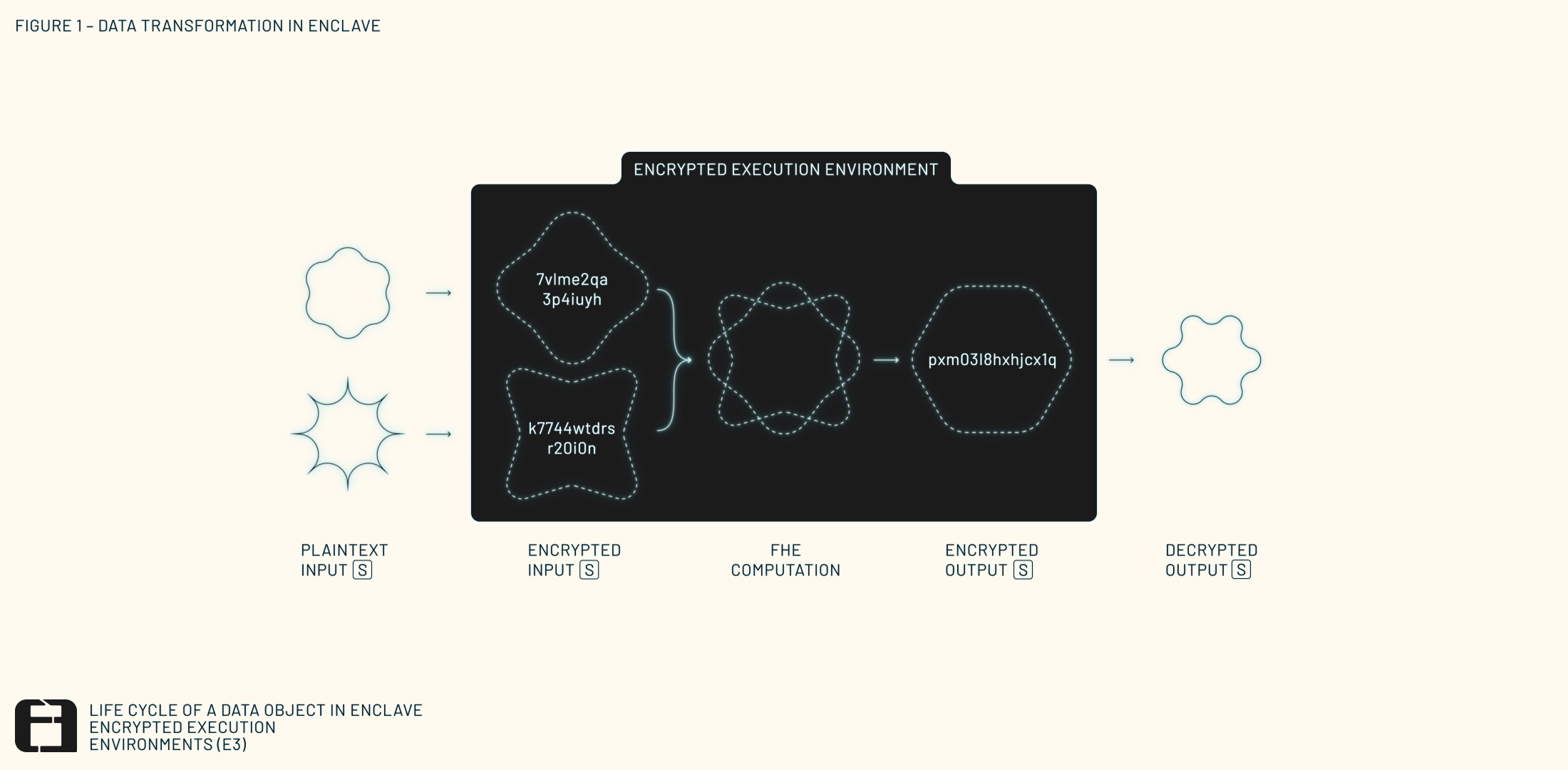
Enclave is the open-source protocol that coordinates the various components necessary to create E3s. These include distributed secret handling, advanced cryptographic techniques, and verifiable computation processes. By distributing trust across a network of nodes, E3s allow organizations to securely leverage their most sensitive data in compliance with privacy regulations, creating use cases previously impossible with traditional solutions.
At the core of this system are three key benefits that define how E3s operate: data privacy, data integrity, and correct execution.
1. Data Privacy: Full Confidentiality Throughout
In E3s, data remains encrypted throughout the computation using FHE, ensuring that no intermediary sees the raw data at any point. This is critical for industries like healthcare and finance, but also for everything from scientific research to auctions and beyond. The ability to compute on multiple inputs of encrypted data without exposure enables a new class of privacy-preserving applications.
2. Data Integrity: Trust Through Cryptography
E3s leverage cryptographic and crypto-economic techniques like zero-knowledge proofs (ZKPs) and distributed threshold cryptography (DTC) to ensure that the data used in computations is valid, authentic, and untampered. These guarantees are essential for environments where data integrity is critical, such as decision-making systems, legal records, or research datasets.
3. Correct Execution: Verifiable Computations
E3s allow participants to select from several different methods to verify the correctness of their computation, either electing to run their computation in a provable environment or relying on an oracle-based solution to report the results. This creates a system where each step of the computation is verifiable, minimizing the risk of compromise and ensuring accurate outputs.
E3 in Context: How it Relates to Other Encryption Technologies
E3 doesn't seek to replace existing encryption techniques but rather extend their capabilities, providing a complete solution in contexts where privacy, security, and trust are critical. Here's how E3 fits within the broader landscape of secure computation:
Fully Homomorphic Encryption (FHE)
While FHE allows computations on encrypted data, it relies on a single decryption key, which introduces vulnerabilities if that key is compromised. FHE is often regarded as the "holy grail" of cryptography, but its reliance on global keys can still lead to security risks.
E3s mitigate this with single-use keys and threshold cryptography to distribute decryption across multiple nodes, eliminating the underlying risks of global keys controlled by a single party. The protocol's ephemeral execution further minimizes these risks, ensuring that keys are only used for the duration of a specific computation request.
Trusted Execution Environments (TEE)
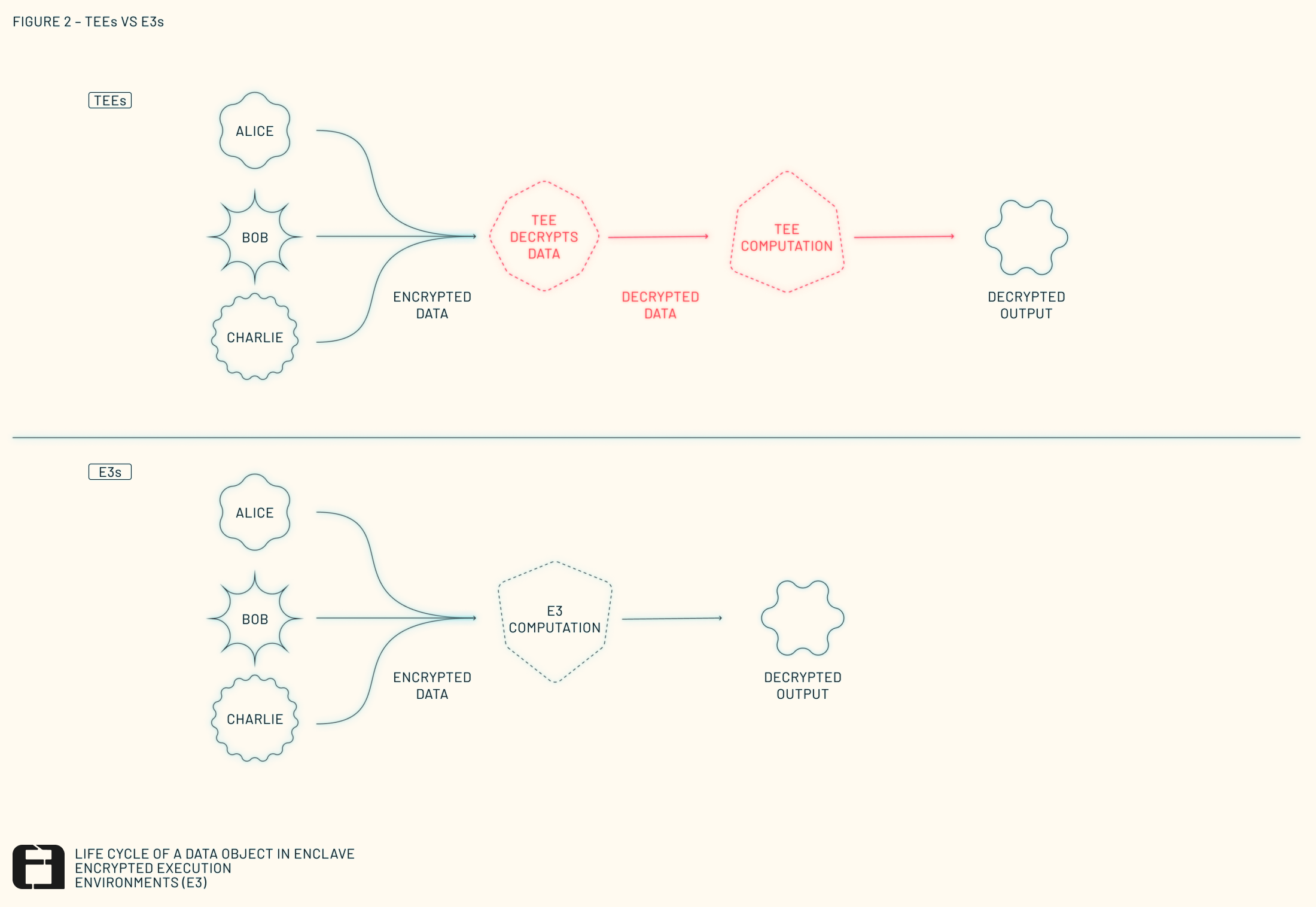
Perhaps the most direct comparison to E3s are TEEs, which are execution environments that utilize trusted hardware to secure computations. However, due to this hardware dependency, they are still vulnerable to side-channel attacks and other forms of exploitation. Academic research has identified over 20 unique styles of attacks on TEEs, exposing weaknesses in memory protection, instruction tracing, and encryption key disclosure.
E3s address these risks by securing computations through distributed threshold cryptography rather than a single piece of hardware. This significantly changes the threat model, ensuring that computations remain secure even if some nodes are compromised (see Figure 2).
Zero-Knowledge Proofs (ZKPs)
ZKPs enable one to efficiently prove things about data without revealing the data itself, making them valuable for many privacy-preserving applications, such as identity verification and financial transactions. However, ZKPs typically require that one party has access to the underlying data to generate the proof, which limits their use in multiparty computations where private inputs need to remain confidential.
With E3s, ZKPs are used to verify the integrity of inputs provided by data sources without exposing private information to anyone or at any point. In addition to input validation, E3s use ZKPs to verify distributed key generation, correct execution, and correct decryption, ensuring secure and confidential multiparty computations that protect inputs and outputs throughout the process.
Cloud Data and End-to-End Encryption
Cloud platforms offer convenience for data storage and processing but often require organizations to place implicit trust in the provider. Despite security measures, data breaches remain a persistent issue, with the average breach cost reaching $4.88M in 2024, according to IBM. Additionally, while traditional methods such as end-to-end encryption protect data in transit, they don’t always safeguard data at rest and during computation, nor do they protect metadata, leaving gaps in overall security.
E3s extend these approaches by keeping the data encrypted throughout the entire computational process, minimizing the need for trust in any single intermediary. This ensures that data remains secure from start to finish, addressing vulnerabilities at every stage.
How E3s Work: The Data Lifecycle in Enclave
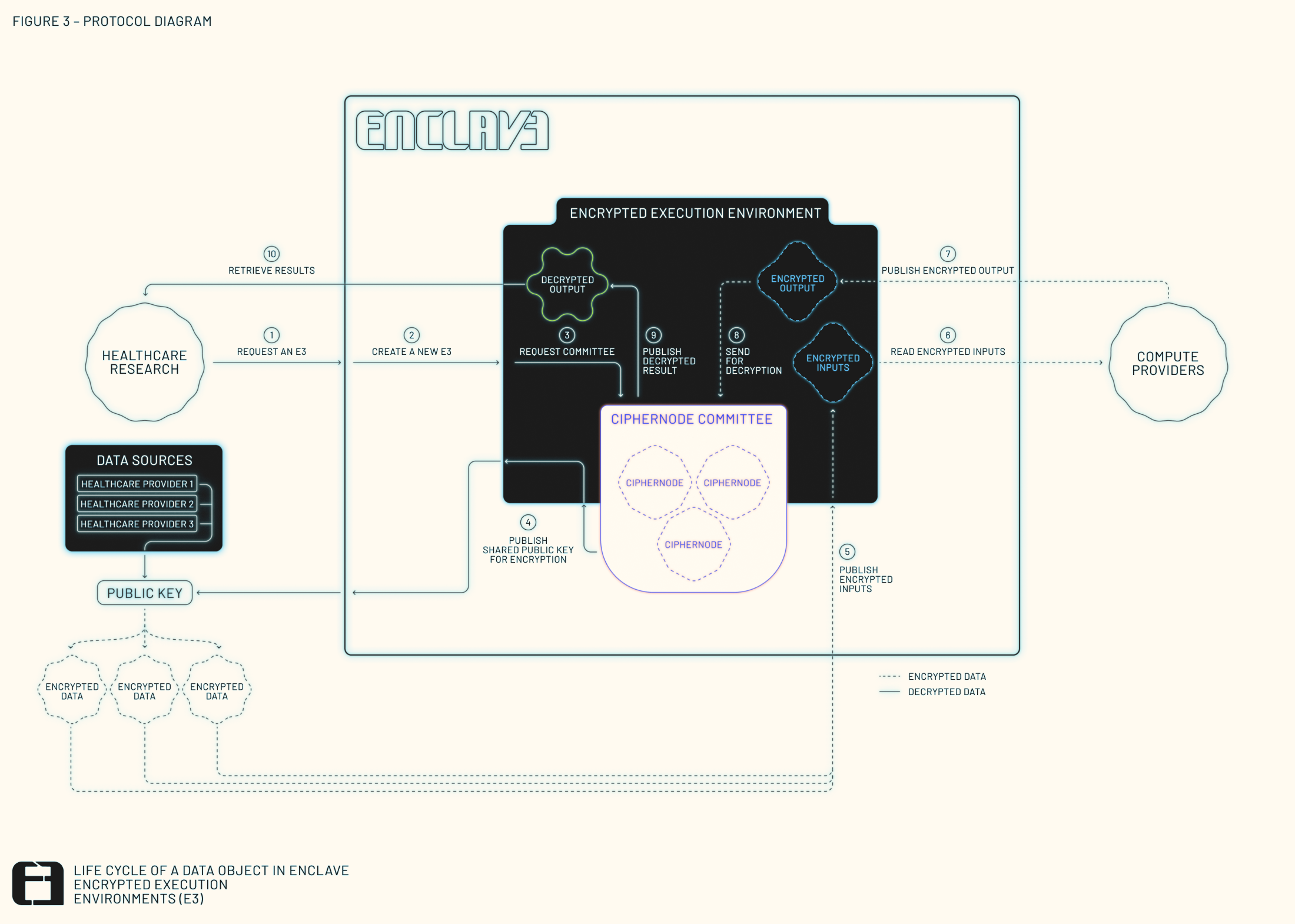
E3s operate through a step-by-step process that ensures privacy and security while allowing computations over encrypted data. Unlike other trust-dependent solutions, Enclave provides strong economic and cryptographic guarantees that inputs and intermediate states remain private throughout their lifecycle, whether it’s a vote in a secret ballot election or private medical data from a healthcare organization. Here’s how it works:
Phase 1: The Request
The process starts when a request is made for a secure FHE computation — for example, to tally private votes or to process private medical data (see Figure 3 above for a visual illustration). This request outlines what kind of data needs to be processed, which compute provider will handle the job (proof-based or oracle-based), the security checks to verify results, and other basic information.
Phase 2: Choosing a Group of Nodes
Once the request is made, a group of nodes is randomly selected through a lottery-like process called sortition. These nodes are responsible for generating and publishing shared encryption keys, which are used to keep the data secure. Because the keys are distributed across multiple computers, no single node can access the entire key. This setup prevents any single party from tampering with the data.
Phase 3: Data Submission
After the keys are set up, the window for submitting data opens. The data providers encrypt their data using the shared key published by the nodes and submit it for processing, with a corresponding zero-knowledge proof for each input. Because the data is encrypted upon submission, no one — not even the computers doing the calculations — can see the raw data.
Phase 4: Running the Computation
Next, the compute provider chosen in Phase 1 executes the computation based on the encrypted data. This is the core part of the process, where the encrypted data is computed and verified according to the instructions specified at the start. Because the computations happen entirely on encrypted data, the data is kept private and secure throughout the process. The computation is then verified through one of the following systems chosen during the initial request:
- Proof-Based Systems (RISC Zero, Succinct’s SP1, Jolt, Nexus): The provider generates cryptographic proofs to show that the computation was performed correctly without revealing the data.
- Oracle-Based Systems (Reality.eth, Kleros Oracle): Some computations may rely on an external verification system, where a consensus mechanism or economic incentives ensure the correctness of the results.
This step ensures the computations are performed securely and accurately, while the data is safeguarded from exposure.
Phase 5: Decrypting the Result
Even though the computation is complete, the result is still encrypted. To unlock it, the group of nodes selected at the start come back into play. They each hold a part of the key needed to decrypt the final result, as reported by the verifiable compute provider. A threshold of the selected nodes must coordinate to reveal the output of the computation. The keys used to encrypt and decrypt are then securely discarded.
The requester — for example, the voting host or the medical researcher — can now retrieve the decrypted result, knowing that the original data was never exposed and that the computations were carried out with guaranteed accuracy.
Real-World Applications of E3s
Encrypted Execution Environments enable a wide range of possibilities across sectors where privacy, integrity, and trust are essential. Enclave's use cases can be categorized under three major sets:
Verifiable Outcomes
In scenarios such as secret ballots or sealed-bid auctions, the legitimacy of outcomes depends on maintaining the confidentiality of inputs while ensuring the integrity of the process. E3s enable secure, decentralized computations that verify results without exposing sensitive data.
Protected Data Access
For organizations that handle sensitive data — such as those specializing in medical research or financial analysis — E3s offer a way to compute over encrypted data without breaching privacy regulations, regardless of who has custody of the data. This reduces liability and ensures compliance with regulatory frameworks like GDPR, enabling safer access and new data-sharing patterns.
Confidential Data Pools
E3s allow multiple organizations and researchers to collaborate securely by contributing sensitive data to encrypted pools, without needing to share raw datasets. This is particularly valuable in fields like genomics or climate science, where privacy, data security, and compliance are critical. E3s open new collaborative design spaces previously impossible due to data sensitivity and regulatory concerns.
A New Computational Ecology is Born
As we begin to comprehend the full potential of computation as today's primary medium — whether to express ideas, enact structural change, or create new forms of art — we need to rethink how we handle the sensitive data that constitutes our systems.
Enclave isn't just about privacy-preserving computations and secure collaborations; it's also about creating new possibilities in how we engage with the data trails we’re constantly generating. By shifting away from traditional data-dependent models and embedding trust directly into its node-based architecture, Enclave reshapes how computation can inform the social, cultural, and political structures that define our digital and physical worlds.
Through this dynamic interplay of interaction and agency, a radically new computational ecology emerges — one where privacy is not supplementary, but foundational for establishing deeper relationality, collaboration, and creative expression in our evolving worlds.
Enclave is an open-source protocol, with Gnosis Guild as its initial development team.
Follow Enclave on social media (X, Farcaster) for updates and subscribe for articles and announcements. For partnership inquires, business opportunities, and more, join the Enclave Telegram group.
