Introducing Ciphernodes: Agents for Encrypted Execution
Ciphernodes are the cryptographic coordination agents of the Enclave protocol. This post introduces what they are, how they work, and how to apply as an early node operator.
Encrypted execution doesn't just happen automatically. It has to be coordinated securely, verifiably, and without exposing sensitive data. In Enclave, this coordination doesn’t rely on trusted hardware or a centralized operator. It’s distributed across a network of cryptographically verifiable nodes.
We call them Ciphernodes.
Ciphernodes are the decentralized backbone of Enclave’s protocol for Encrypted Execution Environments (E3s). They generate keys, secure encrypted inputs, and jointly decrypt results, all without ever seeing the data.
This post introduces Ciphernodes, how they work, and how you can get involved as an Enclave node operator.
Why Coordination Matters for Encrypted Execution
Enclave enables multiparty computation on encrypted data from multiple sources, but without a trusted third party, who manages the keys? Who decides when to decrypt? And how do we verify that no one cheated?
That’s where Ciphernodes come in. Rather than embedding trust in hardware like Trusted Execution Environments (TEEs), Enclave distributes it cryptographically, using staked Ciphernodes selected per job to generate ephemeral threshold keys, validate inputs, and decrypt only outputs. They don’t run the computation, and they never see the plaintext. They just make encrypted execution possible.
What Is a Ciphernode?
A Ciphernode is a staked node in the Enclave network that enables encrypted computation without ever seeing the data or executing the logic. They are fully crypto-economic agents, coordinating and securing encrypted jobs across governance and beyond. Their role is simple but critical: manage keys securely, decrypt results collaboratively.
Each Ciphernode:
🔹 Participates in Distributed Key Generation (DKG) to create a public key for encrypting inputs
🔹 Publishes threshold decryption shares to reconstruct only the final output
🔹 Discards keys after each job, treating them as ephemeral and single-use
Unlike typical blockchain nodes, Ciphernodes don’t validate blocks or maintain state. They don’t run programs, store secrets, or expose data. They exist only for the duration of the compute job, then vanish. This makes them lightweight, verifiable, and free of long-term custody risks.
Where Ciphernodes Fit in the Enclave Protocol
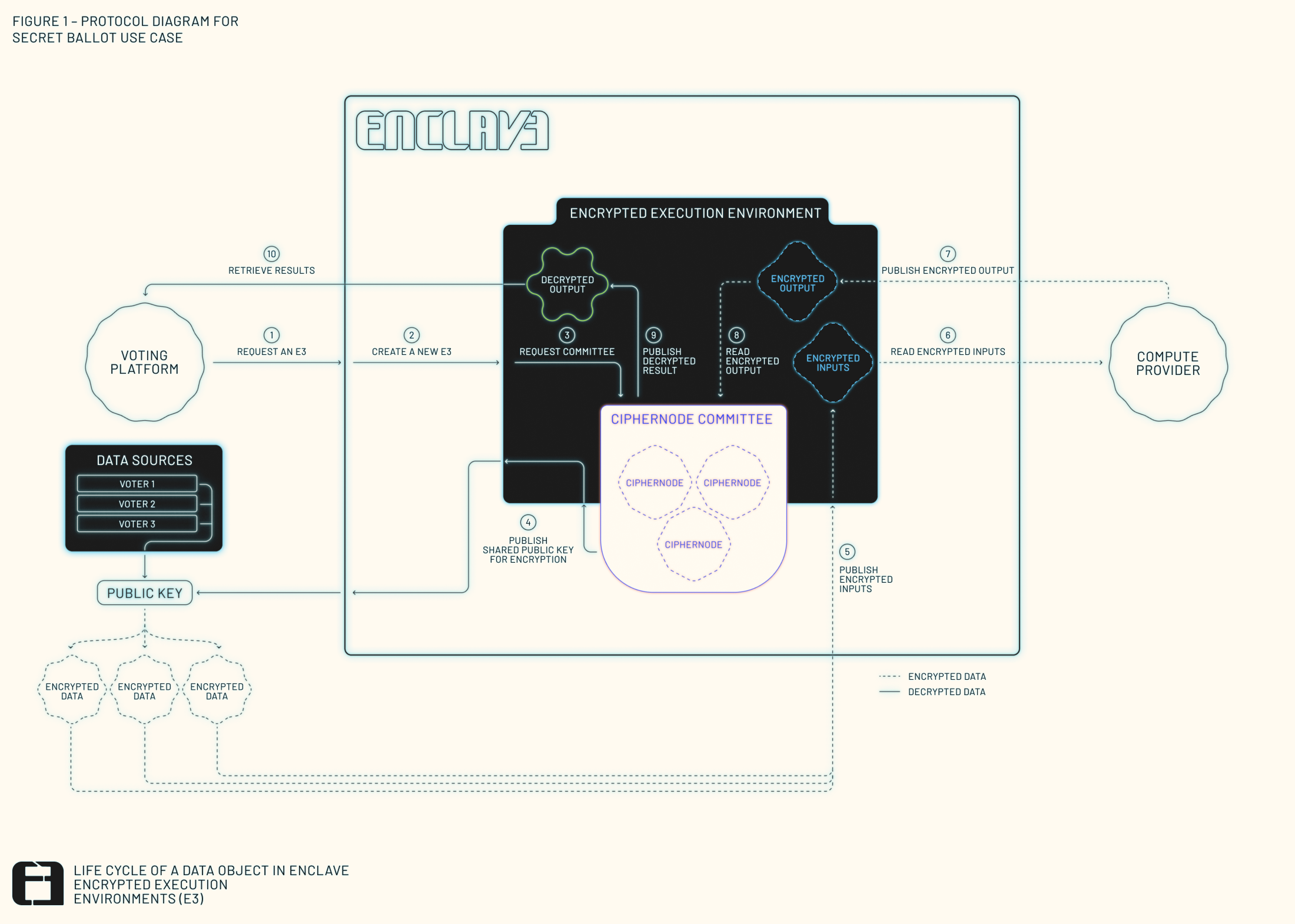
In the lifecycle of an E3, Ciphernodes are activated early and wrap up at the end. Here’s how they fit in:
- Sortition: A random committee of Ciphernodes is selected for each E3.
- Key Generation: The committee runs DKG to produce a shared public key for encryption.
- Encrypted Inputs: Data Providers encrypt inputs using this key.
- Execution: A separate Compute Provider runs the FHE program over encrypted data.
- Decryption: Ciphernodes publish shares to reconstruct the plaintext result.
What You’ll Do as a Node Operator
Ciphernodes are the cryptographic participants that enable encrypted computation in Enclave. To operate one, you’ll stake tokens and take on cryptographic responsibilities within each computation, without ever seeing the data or executing the logic.
Here’s what Ciphernodes do:
🔹 Respond to committee selection (via sortition)
🔹 Participate in DKG to generate encryption keys
🔹 Submit threshold decryption shares when jobs complete
🔹 Maintain uptime and handle ephemeral key disposal correctly
Why This Matters
Ciphernodes aren’t just a technical detail. They’re the foundation of Enclave’s trust model, a way to secure and coordinate encrypted execution without centralized control or hardware-based guarantees.
By distributing key management and verification, Ciphernodes:
🔹 Enable multiparty encrypted computation
🔹 Offer strong guarantees of verifiable outputs without revealing inputs
🔹 Remove the need for trusted hardware or central operators
But cryptography alone isn’t enough. The strength of the system depends on who participates in it. A more diverse, distributed set of node operators makes Enclave more resilient, cryptographically and economically.
In a world where privacy, regulation, and AI coordination are becoming increasingly entangled, Ciphernodes ensure that secure multiparty computation is not only possible, but also programmable, composable, and widely accessible.
What’s Next
Ciphernodes are soon entering their first phase of real-world participation through a permissioned rollout. Selected node operators will help secure and coordinate live encrypted computations while we onboard infrastructure partners and prepare for broader access.
Upcoming features for Ciphernodes include:
🔹 Permissionless registration: anyone will be able to stake Enclave tokens and operate a Ciphernode, with no approvals required
🔹 Token staking, slashing, and rewards: securing jobs and aligning incentives through crypto-economic guarantees
🔹 Dynamic Ciphernode committee sizing: size and selection will adapt automatically based on threshold parameters defined by the requestor
🔹 Improved accessibility: including planned support for tools like DappNode, making it easier for anyone to run a node from home or on edge devices
Apply to Run a Ciphernode
We're inviting a limited number of early node operators to help enable encrypted computation during Enclave's onboarding phase.
If you’re a builder, node operator, infra dev, or just curious about how it all works, dive into the Docs & Tutorials and join the Telegram chat.
